How it works
Cloudproof Encryption is the combination of two cryptographic schemes:
- Covercrypt that provides application level encryption
- Findex that provides encrypted search
Libraries¶
Cloudproof encryption is available in libraries in multiple languages including Java, JavaScript, Python, Flutter and Spark, so it can be embedded in applications to encrypt data as close as possible to its source and decrypt it as close as possible to its consumer.
Get started programming with the APIs by checking these documentation pages:
The libraries are open-source: see Cosmian Github for details.
Key Management System¶
To help manage keys, Cosmian provides a KMIP 2.1 compliant server, see its documentation.
Application Level Encryption¶
The first scheme is a public key encryption scheme that allows encrypting data for a set of attributes in order to provide fine grained partitioning.
Consider the following 2 policy axes, Department and Country which data are partitioned by the following attributes:
Department,Finance,Marketing,Human Res.andSalesCountry,France,UK,SpainandGermany
Each pair (Department, Country) constitutes one of the 4^2=16 data partitions.
With Cosmian attribute-based encryption scheme, the encryption key is public. Encrypting systems (Spark, data engineering applications, ETLs, etc…) do not have to be secured and can directly hold the key, relaxing constraints on the infrastructure. The public key can encrypt for any partition defined by the policy.
Decryption keys can decrypt a subset of the partitions defined by the policy.
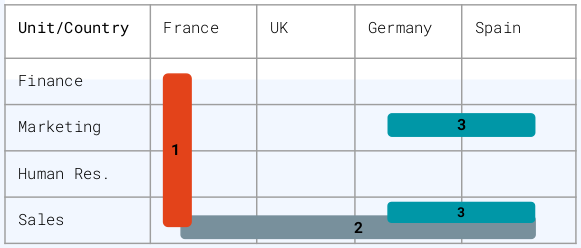
Key 1 can decrypt all the France data with the following access policy:
Key 2 can decrypt all the Sales data with the following access policy:
Key 3 can decrypt the Marketing and Sales data from Spain and Germany with the following access policy:
User keys are truly unique: even though two users have the same access policy, their key fingerprints will be different. This makes it much easier for forensic cyber teams to trace a key leak.
Policy axes can be hierarchical. Suppose three levels on a Confidentiality axis: Medium, Secret, and Top Secret. This hierarchical axis will let users with a Top Secret attribute in their key access policy decrypt Medium, Secret, and Top Secret data – whereas users with a Medium attribute will only be able to decrypt Medium data.
Finally, attributes can be rotated providing forward secrecy on selected partitions only.
Encrypted search¶
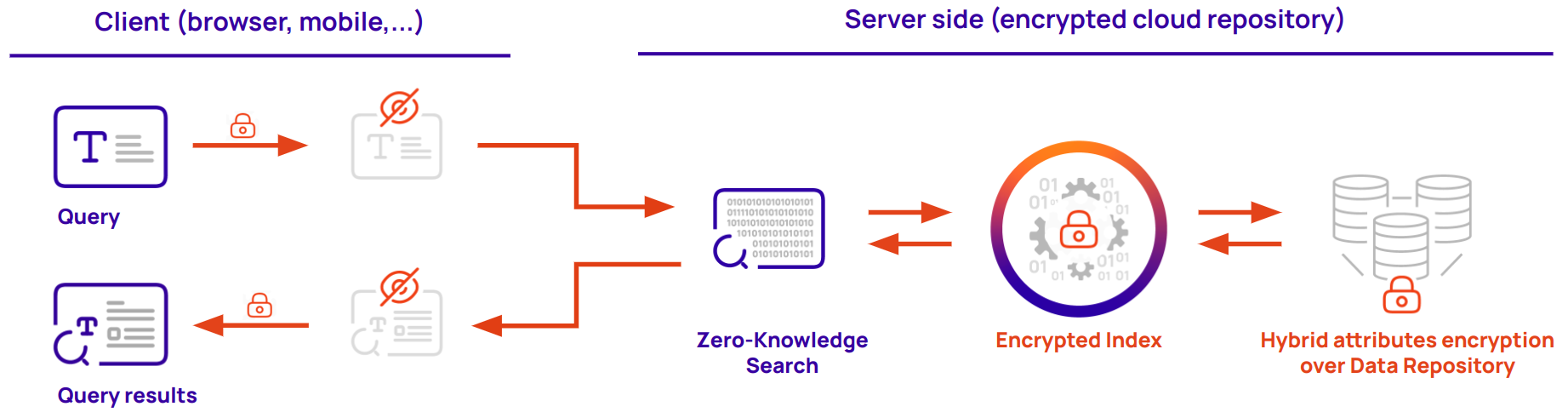
In addition to encrypting the data given access policies, Cosmian Cloudproof Encryption libraries offer the ability to create encrypted indexes and securely search for encrypted data.
These indexes match an encrypted keyword to an encrypted location (a database UID, an URL…). The encrypted search can handle exact match, starts-with, ends-with and synonyms.
Encrypted indexes have the following characteristics:
- all data in the indexes are encrypted
- queries to the index are encrypted
- answers to queries are encrypted
Since the server never learns anything about the content, the queries or the answers, so the index can be safely stored in a zero trust environment, next to the indexed data. Typically, these indexes are stored in fast scalable key-value stores deployed in the cloud.