Overview
Cosmian Enclave allows to quickly deploy confidential Python web applications with the following security features:
- Code runs in a Trusted Execution Environment (TEE) and is encrypted with your key.
- Secure channel is established directly and uniquely with your code running inside the TEE.
- The integrity of the code loaded in TEE’s memory is verifiable through a remote attestation process.
- Everyone interacting with your application can verify that your code runs in a TEE thanks to a Transport Layer Security (TLS) extension called Remote Attestation TLS (RA-TLS).
Use Cases¶
Two common use cases of Cosmian Enclave are:
- Offer confidential AI/ML SaaS services to your customers while guaranteeing their data cannot be accessed by you or by the cloud provider.
- Deploy confidential code, models, and/or data in a Zero-Trust environment, where you have zero control over the infrastructure and its administration. For instance, an AI company deploying a fine-tuned model in a customer’s infrastructure wants to keep the code and model secrets.
Security guarantees¶
Cosmian Enclave protects data and metadata against system administrators with root access and the underlying cloud provider who owns the hardware infrastructure.
Then, privileged users or anyone with physical access to the host machine:
- Cannot alter the integrity of data and code in the protected area of the TEE.
- Cannot access your application’s unique TLS server key generated inside the TEE or decrypt the TLS session.
- Cannot decrypt your encrypted code or access the secret key.
- Cannot access the persistent storage of your application tied to the TEE and the fingerprint of your application.
These assumptions remain valid as long as the TEE hardware, namely Intel SGX, and its software stack known as the Trusted Computing Base (TCB) are not subject to severe vulnerabilities.
Cloud provider availability¶
As of August 2024, Microsoft Azure, Alibaba Cloud and OVH Cloud offer Intel SGX processors with SGX2 capability. Microsoft Azure and Alibaba Cloud provide VM-based instances with the SGX driver loaded while OVH Cloud provides dedicated servers with Intel SGX processors.
Bare Metal requirements¶
Cosmian Enclave requires Intel Xeon 4th or 5th-gen processors with SGX2. To find all the compatible Intel processors, see Intel Processors supporting Intel SGX.
Workflow¶
The following diagram illustrates the scenario with two roles:
- The SGX operator who is the administrator of the SGX machine and the one going to run the confidential code
- The code provider who writes the Python code and sends it encrypted to the SGX operator
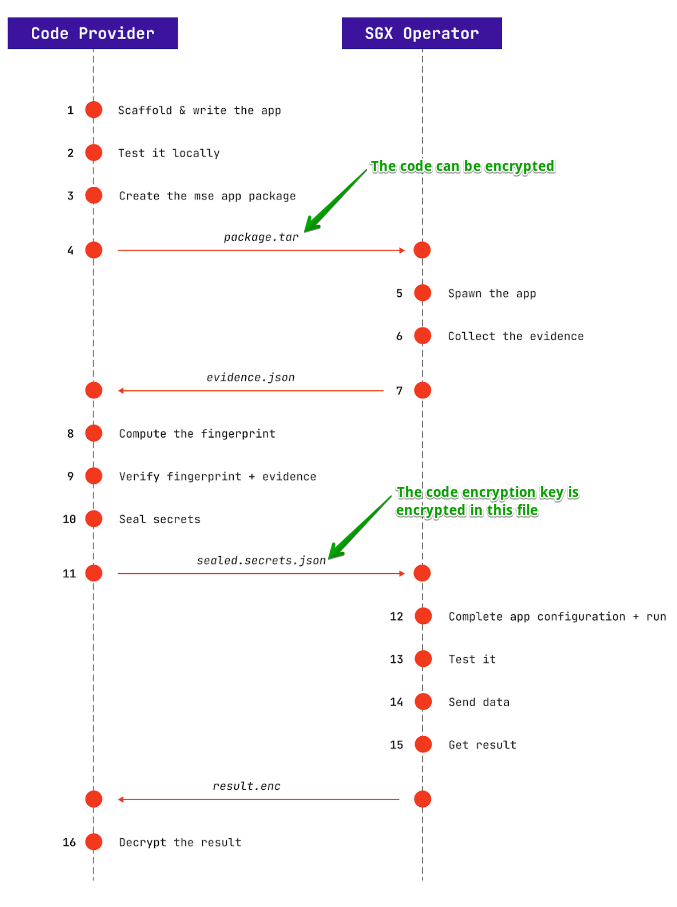
- The Python code must be an ASGI application using Python web framework such as Flask or FastAPI. It can be optionally encrypted with a random key using the Cosmian Enclave CLI with
--encryptargument. - Since the code is encrypted under a key you only know, the code can be transmitted through any channel, even insecure.
- Using the CLI, The SGX Operator loads the encrypted code in a new Cosmian Enclave. It outputs an
evidence.jsonfile, which should be returned to the code provider. - The code provider verifies the evidence file using the CLI. It ensures that the correct code is loaded in a fresh new Cosmian Enclave and has not been tampered with. This process, called the remote attestation, also verifies if the TEE is genuine and will tell you if there are known vulnerabilities on the remote server’s Trusted Computing Base. The file also contains a public key whose corresponding private key is only known to your Cosmian Enclave and cannot be recovered by the SGX Operator.
- Using the unique enclave’s public key tied to your code, the code provider encrypts a
secrets.jsonfile that contains the code decryption key and any other secrets specific to your application. - The enclave can now decrypt the code inside Intel SGX encrypted memory and run it.
The provider can send data to the application’s endpoints over a secure RA-TLS channel directly with the enclave.